Overview
The expected benefits
Together, let’s harness the full potential of the European payment account information opening.

This AISP PSD2 API product allows you to securely access transaction data for customer payment accounts from all institutions within the Caisses d'Epargne network.
Secure Data Access
Access customers' payment account information through a secure and regulatory-compliant device.
Value Creation
Enhance your offerings and products to better serve your clients through innovative use cases.
The connection is made through a secure device compliant with European regulatory requirements. By accessing this account information service, your customers will be able to view their payment account information within your environment: account list, balances, transactions (date, description, and amount), etc.
You will thus be able to enhance the added value of your products/services to serve your clients through innovative use cases: account consolidation, accounting reconciliation, customer knowledge enrichment, budget analysis and forecasting, etc.
The different possible use cases
Together, let's create value for our shared clients.
Consolidation
Allow your clients to aggregate their payment accounts to have a consolidated and real-time view of their transactions.
Accounting Reconciliation
Enable your corporate clients to reconcile their invoices and business expenses with their payment transactions.
Customer Insights
Understand and learn from the payment behavior of your individual or corporate clients.
Business Management
Leverage customer payment data to build high-value management dashboards.
How to access the product ?
To access the Account Information Services API, developers and businesses must follow the steps below.
Contact
Get in touch with the product managers.
Access
Enroll directly through the dedicated process (regulated entities).
Integration & Testing
Integrate our service into your solution and share your use cases with us to help ensure the quality of our offering.
Go Live !
Documentation
Guides
How to agregate data ?
A customer having different accounts in various banks is willing to agregate his data.
Using this API “Account information” setup by banks (ASPSP), you can ask for real-time data authorized by the customer without asking for online banking credentials.
The API resources can only be consumed if you have obtained the Account Information Services Provider (“AISP”) role status. This prerequisite is described in section “Eligibility“.
Once done, the overall process is as follows :
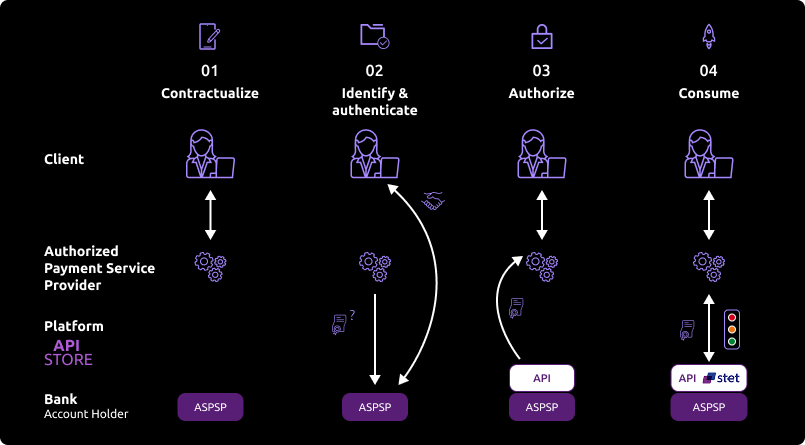
The customer agreed to use your service. He needs to select his ASPSP through your interface.
During the first set of data exchanges, you will request for an authorization token (and a refresh one). For this AISP role, you need these tokens BEFORE consuming API resources. These tokens are issued by the ASPSP AFTER an identification and authorization process of the bank accound holder.
The ASPSP will :
- check your certificates and on-going agreement delivered by the Comptent Authority
- identify and authorize the customer using the “redirect” mode in order to issue the tokens.
If the above access is granted by the customer, you can then get these OAuth2 tokens thru secure exchanges (see use case “Get your token“).
Whenever you present this token to the BPCE API gateway, you will be able to consume this API resources in order to :
- request for the list of eligible accounts (see use case “List accounts“)
- forward customer’s consent to the ASPSP (see use case “Forward customer’s consent“)
- securely access to granted customer’s data (see use case “Access to data“)
If the regulated 180-day token validity period expires, this process needs to be started again (see use case “Refresh your token“)
Note : any ASPSP can refuse the access to customer’s data for any justified reason (non compliant API call, blocked account, …).
Access to data
In order to query an API, the API version is included in the URI such as : /stet/psd2/v1.6.2/accounts.
The features are described hereafter only from a functional standpoint. The technical aspects are included in the section « Technical use cases ». You also need to be familiar with PSD2 terminology. You may also use the Frequently Asked Questions (FAQ).
As a reminder, this API is designed to give access to payment accounts (and to a predefined set of data) granted by the customer :
- balance
- and/or transactions history + details if available
- and/or connected customer
- and/or overdraft
Some of these services may have some contraints or may not be available if not present in the online banking environment.
In sandbox assembly mode, access to tests data can be done thru the endpoint www.<codetab>.sandbox.api.89C3.com (see use case « Test our API »).
In production, acces to live data can be done through the endpoint www.<codetab>.oba-bad-me-live.api.89C3.com (see use case « Limits») (new URL to be taken into account from now on)
(As a reminder, the existing URL www.<codetab>.live.api.89C3.com will no longer be available as of 28/09/2025).
Get the list of eligible payment accounts
Description
This first call allows to get the list of eligible payment accounts when the user of payment services (PSU) is using services from a third party provider (TPP AISP) connected to the bank account holder (ASPSP).
Prerequisites
- TPP has an agreement for the AISP role from any european competent authority ;
- TPP and PSU have service contract ;
- A OAuth2 access token has been delivered to the TPP by the ASPSP ;
- TPP and ASPSP have been performed a mutual authentication ;
- TPP has delivered his OAuth2 access token to be able to consume the API resources.
Transaction flow
TPP is interacting with the customer thru its interfaces. TPP sends a GET request to ASPSP infrastructure to get this list of accounts, which returns the eligible payment accounts.
Customer consent
Description
This second request is mandated by the ASPSP : TPP has requested the customer to give his consent on the accounts he wants to use (ans which data).
This information (list of authorized accounts and data) needs to be sent back by the TPP to the the bank (ASPSP) for recording this customer consent. This “consent” record is linked only to a given PSU + given TPP AISP + given authorized payment account(s) + given authorized data for each account. The ASPSP will verifiy each TPP access request to the accounts vs. this record.
This consent can be modiifed at any time by calling again this service.
Prerequisites
TPP has requested the list of accounts for the first time.
PSU give his consent to AISP.
Transaction flow
TPP AISP forward these authorized data to the bank (ASPS) using a PUT request
Get balance
Description
This call allows to get the accountable balance (“CLBD” in STET specifications).
Prerequisites
TPP has requested the list of accounts and sent PSU consent to ASPSP.
Transaction flow
AISP requests the ASPSP to send back the balance of one of the authorized accounts.
Get transactions history
Description
This call allows to get the 90-day transactions history.
Prerequisites
TPP has requested the list of accounts and sent PSU consent to ASPSP.
Transaction flow
AISP requests the ASPSP to send the transaction histroy with some criteria.
Get PSU identity
Description
This call allows to get the connected customer identity.
Prerequisites
TPP has received PSU consent of this data and sent it to ASPSP.
Transaction flow
AISP requests the ASPSP to send PSU identity data.
Get PSU overdraft
Description
This call allows to get the account overdraft.
Prerequisites
TPP has requested the list of accounts and sent PSU consent to ASPSP.
Transaction flow
AISP requests the ASPSP to send overdraft data.
How to use the fallback mode ?
Principle
In order to comply with PSD2 regulations, banks available on this BPCE API developer portal have setup contingency measures in case of unplanned unavailability of the dedicated API interface.
The principle of this « fallback » solution is explained below:
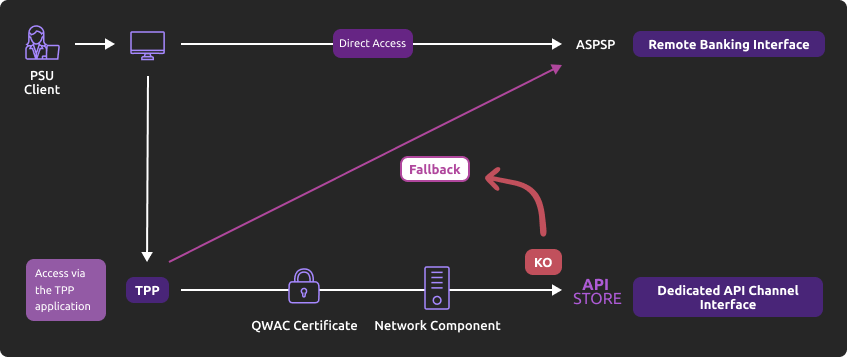
This fallback mechanism meets PSD2 regulatory requirements (article 33/RTS). It can be used with the same conditions and prerequisites applicable for the dedicated API interface which are specified in the “Eligibility” use case.
Roadmap
Please do find below our estimated roadmap :
| Version | Features | Sandbox Deployment BPCE API Dev Portal & Sandbox | Live Deployment BPCE Live API Gateway |
|---|---|---|---|
| v1.0 | Fallback (*) | Not applicable | End of September 2019 |
(*) Main features :
- Use the same API dedicated interface endpoint. The list of our banking institutions and the possible values of <bkcode> are specified in the “Limitations” use case
- A parameter (header ‘fallback:1’ present or absent) managed directly by the TPP allows do differentiate any « Fallback » request from dedicated interface PSD2 API requests
- Use of same TPP eIDAS certificate (QWAC) to be presented for mutual TLS authentication
- Use the same PSU authentication procedure and means for accessing online banking services
- This fallback solution is always active, even so the dedicated interface API must be used systematically in first priority. Its usage is subject to strict conditions as described in Article 33 of RTS, and can’t be used as the main access for PSD2 features. It will be monitored as such and every abuse will be automatically reported to our national competent authority
Example
1. If PSD2 API are not available due to unplanned unavailability or systems breakdown (see RTS Art. 33), TPP should use the following request qith <codetab>=17515 as an example :
POST https://www.<codetab>.oba-bad-me-live.api.89c3.com/stet/psd2/oauth/token
(new URL to be taken into account from now on)
(As a reminder, the existing URL www.<codetab>.live.api.89C3.com will no longer be available as of 28/09/2025)
with :
- its live eIDAS QWAC certificate
- fallback:”1″ parameter in the header
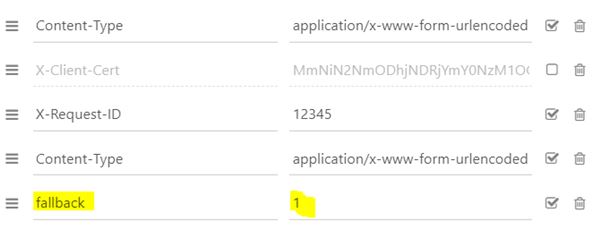
POST /stet/psd2/oauth/token HTTP/1.1
Content-Type: application/x-www-form-urlencoded
X-Request-ID: 1234
fallback: 1
User-Agent: PostmanRuntime/7.16.3
Accept: */*
Cache-Control: no-cache
Host: www.17515.oba-bad-me-live.api.caisse-epargne.fr
Accept-Encoding: gzip, deflate
Content-Length: 67
Connection: keep-alive
client_id=PSDFR-ACPR-12345&grant_type=client_credentials&scope=aisp
2. If all checks are successful, the TPP will receive in the header of the response with url online (allowing to access banking login web page) as well as the JWT token to be used also in the rediction process.
HTTP/1.1 302 Found
Date: Tue, 25 May 2021 21:46:59 GMT
Content-Length: 870
Connection: close
Content-Type: text/html; charset=iso-8859-1
</head><body>
<h1>Found</h1>
<p>The document has moved <a href=”/www.17515.live.api.caisse-epargne.fr&fallback=eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsIng1dCI6ImhF…”>here</a>.</p>
</body></html>
3. Once redirected, the TPP must then use the PSU's credentials via its proprietary method.
For more details about POST request, see STET specifications
Please note the following constraints which apply on this fallback mechanism :
- No re-use of the API dedicated interface context, neither any of 180-day validity access token generated for AISP role
- Only online internet banking features are used as a reference (excl’d mobile banking features) and are accessible thru the fallback mode. As an example, online banking doesn’t propose any e-commerce transactions to customers. PISP could NOT propose this feature in fallback mode
- The user of payment services (PSU) must be connected to PSP app. So no AISP batch process is possible
- PSD2 also imposes a reinforcement of strong customer authentication (SCA) for accessing direct online banking services. Therefore fallback mechanism leverages on reinforced PSU online banking authentication procedures and means such as (non exhaustive list) :
- Soft token Secur’Pass on smartphone
- Password + OTP SMS
- Physical token (corporate market)
Trigger App2App feature
Introduction
This service allows you to activate automatically (without PSU action) the banking app on PSU smartphone for identification and authentification process.
Prerequisites
The PSU has to load and to use at leat once the latest retail banking mobile app (V6.4.0 and higher) available on Android and Apple app stores.
Note : PRO & ENT customer segments are not yet activated
The callback universal link (same principe as url callback) shall be definied in advance by the TPP :
- if this link/url already exists on our BPCE API gateways, there is nothing else to do
- otherwise the TPP shall declare it using our PSD2 Registration API
Our “Universal links” links have been declared on iOS & Android platforms. It is not worthwhile to access to them e. g. using https://www.<codetab>.oba-bad-me-live.api.caisse-epargne.fr/89C3api/accreditation/v2/.well-known/apple-app-site-association which sends back an error code.
(new URL to be taken into account from now on)
(As a reminder, the existing URL www.<codetab>.live.api.89C3.com will no longer be available as of 28/09/2025)
Request
PSU banking app activation can be achieved in live production using a current STET API request (initiated by the TPP app on the same smartphone device) with the following endpoints :
| Brand | App2App endpoint |
|---|---|
| Banque Palatine | http://www.40978.live.api.palatine.fr/stet/psd2/oauth/authorize |
| Banque Populaire | http://www.<codetab>.live.api.banquepopulaire.fr/stet/psd2/oauth/authorize (see the list of <codetab> on the Banque Populaire API product sheet) |
| Banque de Savoie | http://www.10548.live.api.banque-de-savoie.fr/stet/psd2/oauth/authorize |
| Caisse d'Epargne | http://www.<codetab>.live.api.caisse-epargne.fr/stet/psd2/oauth/authorize (see the list of <codetab> on the API Caisse d’Epargne product sheet) |
| Banque BCP | http://www.12579.live.api.banquebcp.fr/stet/psd2/oauth/authorize |
| Crédit Coopératif | http://www.42559.live.api.credit-cooperatif.coop/stet/psd2/oauth/authorize |
| BTP Banque | http://www.30258.live.api.btp-banque.fr/stet/psd2/oauth/authorize |
| Natixis Wealth Management | http://www.18919.live.api.natixis.com/stet/psd2/oauth/authorize |
Otherwise, a webview will be displayed on PSU smartphone web browser if :
- the banking app is not present on PSU device nor App2App compliant (not the latest version uploaded, see prerequisites)
or
- the other endpoint format is used www.<codetab>.oba-bad-me-live.api.89c3.com/stet/psd2/oauth/authorize (can be used as a backup in case of App2App problem)
Regulatory Publications
Get your token
Principle
Access to PSD2 API features is granted by the bank with an authorization token (or access token) issued using OAuth2 standardized process.
How it works
See also STET specifications
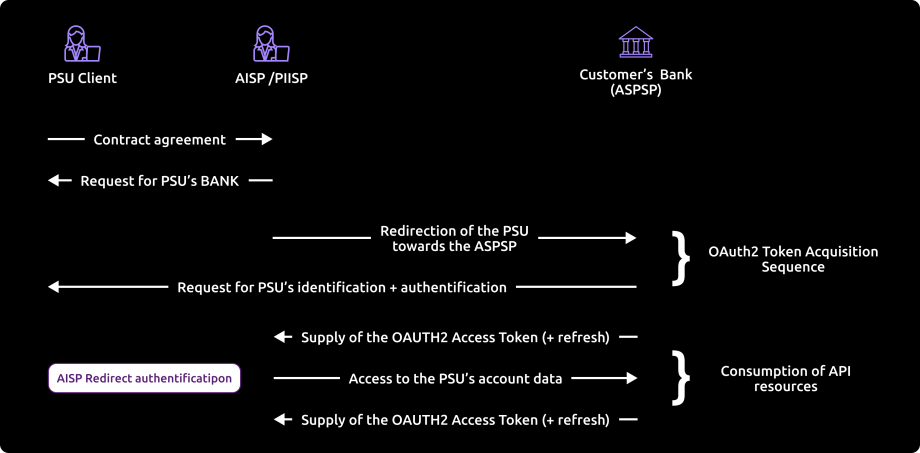
1- The customer (PSU) provides the identity of the bank which holds his accounts (ASPSP) to the TPP.
2- The TPP initiates an OAuth2 access token request sequence by redirecting the customer to the ASPSP’s authorization infrastructure using GET /authorize
See also STET specifications
3- ASPSP will :
- Identify and authenticate the PSU
- Check your role and validity of your eIDAS certificates and agreement
4- Once checks are done and correct, ASPS will redirect the PSU to your site using “call-back” URL given in the GET /authorize and to ASPSP for the Go Live process.
You will find in the response of this request a one-time-token with a short life period.
5- You can then call the ASPSP in order to request the OAuth2 token (and refresh one) using POST /token with previously received data (incl’d the one-time-token).
Note : these /token requests for getting the Authorization Code flow shall be sent WITHOUT the « scope » parameter.
See also STET specifications
6- ASPSP will :
- Check your role and validity of your eIDAS certificates and agreement
- Checks the direct or indirect matching between the Authorization Number within the eIDAS certificate and the [client_id] value
7- Once checks are done and correct, ASPSP returns a response HTTP200 (OK) with data including the access token.
See also STET specifications
8- As soon as you get the OAuth2 access token (and a 180-day valid refresh token) issued by the bank, you can use it for each API request within the “Authorization” header, prefixed by the token type “Bearer”.
The [client_id] that is linked to the access token must directly or indirectly match with the Authorisation Number that is located within the TPP’s eIDAS certificate (QWAC).
If the access token is expired, the request will be rejected with HTTP401 with an error equal to “invalid_token”.
The request can be replayed once the access token has been refreshed suing the use case “Refresh your token“.
If your refresh token is about to expire, you will have to perform again all this process, meaning also redirect to ASPSP for customer’s strong autentication (PSU SCA).
For more details, see also OAuth 2.0 Authorization Framework : https://tools.ietf.org/html/rfc6749#section-4.1
Example
You can find an example of this request in section “Test our API” and then “Sandbox“.
Get accounts list
Principle
Using this service, you can get access various data from a payment account authorized by the customer :
- list all eligible online accessible payment accounts
- retrieve accounting balance
- get URI for the GET /end-user-identity method
- get URI for GET /balances, GET /transactions, GET /details & GET /overdrafts methods
Access to this method is limited to a maximum of 4 batch per day for a given TPP + ASPSP + account + PSU (except if the PSU is connected and has requested this operation).
Prerequisites
In order to proceed, TPP needs to fulfill all eligibility criteria and to present a valid OAuth2 Authorization token (see use case “Get your token“).
Request
Method “GET /accounts”
See also STET specifications
Returned result
IF YOU USE THIS METHOD FOR THE FIRST TIME
(therefore if you didn’t send previously any information using PUT /consents, OR if all granted accounts have not been revoked using PUT /consents – see use case “Forward customer’s consent“) :
This call allows you to list all eligible online accessible authorized payment accounts (incl’s new ones) from our customer (without balances, URI or ressourceID) for the following methods :
- GET /balances
- GET /transactions & GET /details
- GET /overdrafts
IF YOU HAVE ALREADY FORWARDED AT LEAST ONE CONSENT FROM THE CUSTOMER USING PUT /CONSENTS
(therefore if you have used previously PUT /consents request, OR if all granted accounts have not been revoked using PUT /consents – see use case “Forward customer’s consent“) : this call allows you to retrieve all eligible online accessible authorized payment account with the following additional data :
- Accounting balance if this account is flagged in the “balances” parameter in PUT /consents method
- URI for the GET /balances method if this account is flagged in the “balances” parameter in PUT /consents
- URI for the GET /transactions & GET /details (if available) methods if this account is flagged in the “transactions” parameter in PUT /consents
- URI for the GET /overdrafts method if this account is flagged in the “overdrafts” parameter in PUT /consents
Note : The « currency » paramater is now inserted in « accountId » field
Example
You can find an example of this request in section “Test our API” and then “Use our sandbox“.
Acceptance tests
The purpose of these tests is to ensure that the API complies with the STET standard. They should be validated before any application deployment.
| Description | Test data |
|---|---|
Get all PSU payment accounts
| PSU Persona : CLAIRE PSU context = BY-AISP scope OAuth2 = aisp Result: message HTTP 200 => OK with 2 accounts returned |
HTTP request with non autorized access token for this resource (wrong scope)
=> check if HTTP 403 is returned (access refused)
| PSU Persona : LEA PSU context = BY-AISP scope OAuth2 <> aisp Result : Error message HTTP 403 returned |
Use a non authorized request (POST)
=> check if HTTP 405 is returned
| PSU Persona : LEA PSU context = BY-AISP scope OAuth2 = aisp Result : Error message HTTP 405 returned |
Forward customer's consent
Introduction
This service is mandatory as required by Caisse d’Epargne ASPSP as part of the “Mixed” model.
Prerequisites
It is necessary to fulfill the eligibility prerequisites and to have retrieved the OAuth2 access token (see the “Overview“> “Recover your token” section).
You can retrieve the list of the customer’s eligible payment accounts after calling the GET /accounts request for the first time: you will find the IBAN associated with each account, ie “accountId”: {“iban”: ” “}.
However, if you already know the IBAN (s) for the customer’s payment accounts, you can send them to us directly via the PUT / consents method.
WARNING: as long as you have not communicated to the account keeper (ASPSP) at least one account authorized with the PUT /consents method, or if no account is authorized, this GET /accounts method will not return the information requested but only the list of all current accounts included new ones (principle of “AISP mixed consent”).
Request
Method “PUT /consents”
See also STET specification
The PSU specifies to the AISP which of his/her accounts will be granted and which data should be available : it gives his consent and included four access types (or operation types) :
- balances : access to one or many PSU accounts balance report
- transactions : access to one or many PSU accounts transactions history and details (if available)
- psuIdentity : access to connected PSU identity (name & surname for retail customer, ot corporate ID for a company)
- overdrafts : access to PSU accounts overdraft
Note : the following methods are NOT supported
- GET /trustedBeneficiaries : whatever value is used (True/False), it won’t be taken into account
- GET /owners : whatever value is used, it won’t be taken into account
The AISP forwards details of PSU consent to the ASPSP through this call.
Each new API request calls the ASPSP consent service, for one given PSU, replaces any prior consent that was previously sent by the AISP.
Furthermore, upon the PSU’s request, the consent may be updated subsequently for an operation type : for example, access to transactions can be revoked while access to balances stay active :
- If no accounts is transmitted with PUT /consents method, and if a consent was given previously for some accounts using this method, then it means that the customer is revoking all his accounts
- If no accounts is granted, or if the customer has revoked all this consented accounts, the GET /accounts method allows to get all the accounts list (included new ones) but access to related data (balances, transactions) is NOT anymore possible
- In order to get any new account, a PUT /consents with no data is necessary
Example
You can find an example of this request in the section “Test our API” and then “Use our sandbox“. The test data sets are described in the section “Test our API” and then “Test with persona“.
See also STET specification
Acceptance tests
The purpose of these tests is to ensure that the API complies with the STET standard. They should be validated before any application deployment.
| Test description | Nature of the test | Data set |
|---|---|---|
| Add / update the consent of a customer=> HTTP code 201 is returned | Mandatory | Persona : LEA IBANs : FRxxx FRxxx Result : HTTP code 201 is returned |
HTTP request with an access token which is not authorized to access to this resource (incorrect scope) => Access to the resource is not allowed (HTTP code 403) | Mandatory | Persona : LEA Result : HTTP code 403 is returned |
HTTP request using POST method =>HTTP code 405 is returned | Mandatory | Persona : LEA Result : HTTP code 403 is returned |
Get account balance
Introduction
Using this service, you can get the accounting balance data (“CLBD” in STET) on a payment account granted by the customer.
It follows the return of the list of current accounts for a customer : a resource identifier corresponding to an account must be provided to obtain the corresponding accounting balance.
Access to this method is limited to a maximum of 4 batch per day for one given TPP + ASPSP + account + PSU (except if the PSU is connected and has requested it).
Prerequisites
The TPP has previously retrieved the list of available accounts for the PSU :
- Customer’s IBAN should have been forwarded to ASPSP in the “transactions” list of the PUT /consents method (see use case “Forward customer’s consent“)
- The “accountResourceId” is sent in the GET /accounts response / field “resourceId” for this IBAN
- URI or accessing this method is given using the field “_links”: {“transactions”: {“href”: …}} as a response of the GET /accounts using above “accountResourceId”
Request
Method “GET /accounts/{accountResourceId}/balances”
See also STET specification
Mandated parameter
“accountResourceId” : current account for which you want to retrieve transactions history.
This field corresponds to the field “resourceId” obtained in the GET /accounts request result page.
Example
You can find an example of this request in section “Test our API” and then “Use our sandbox”.
See also STET specification
Acceptance tests
The purpose of these tests is to ensure that the API complies with the STET standard. They should be validated before any application deployment.
| Description | Test data |
|---|---|
Get accounting balance => Check negative balance | PSU Persona : LEA PSU context = BY-AISPscope OAuth2 = aisp Result : message HTTP 200 => OK negative balance returned |
Get accounting balance from an unkown account => check if HTTP 404 is returned | PSU Persona : unkown – CPT30014684067 PSU context = BY-AISP scope OAuth2 = aisp Result : Error message HTTP 404 returned |
HTTP request with non autorized access token for this resource (wrong scope) => check if HTTP 403 is returned (access refused) | PSU Persona : LEA PSU context = BY-AISP scope OAuth2 < > aisp Result : Error message HTTP 403 returned |
Use a non authorized request (POST) => check if HTTP 405 is returned | Persona : LEA PSU context = BY-AISP scope OAuth2 = aisp Result : Error message HTTP 405 returned |
Get accounting balance => Check null balance
| PSU Persona : CLAIRE FR7617515900000400358074026 PSU context = BY-AISP scope OAuth2 = aisp Result : message HTTP 200 => OK null balance returned |
Get accounting balance => Check positive balance
| Persona : CLAIRE FR7617515900000800358074006 PSU context = BY-AISP scope OAuth2 = aisp Result : message HTTP 200 => OK positive balance returned |
Get transactions history
Introduction
Using this service, you can get the transactions history data (& details if available) on a payment account granted by the customer.
The type of account is an elligible PDS2 payment account (either a deposit account for individuals, or a current account for professionals and legal entities).
Prerequisites
The TPP has previously retrieved the list of available accounts for the PSU :
- Customer’s IBAN should have been forwarded to ASPSP in the “transactions” list of the PUT /consents method (see use case “Forward customer’s consent“)
- The “accountResourceId” is sent in the GET /accounts response / field “resourceId” for this IBAN
- URI or accessing this method is given using the field “_links”: {“transactions”: {“href”: …}} as a response of the GET /accounts using above “AccountresourceId”
Request
GET /accounts/{accountResourceId}/transactions
GET /accounts/{accountResourceId}/transactions/{transactionResourceId}/details (method to call for each transaction details if they are available)
See also STET specifications
Mandated parameters
“accountResourceId” : current account for which you want to retrieve transactions history.
This field corresponds to the field “resourceId” obtained in the get/accounts request result page.
Optional parameters
- dateFrom : start date to search for transactions (date included)
- dateTo : end date to search for transactions (date NOT included)
- PSU-IP-ADDRESS => to be inserted in the header if the PSU is connected to AISP services
- entryReferenceFrom => NOT used by this API
- entryReferenceTo => NOT used by this API
- dateType => NOT used by this API
The date format for “dateFrom” & “dateTo” is based on ISO 8601 standards with the three following allowed formats :
- YYYY-MM-DDTHH:MM:SS.SSS or YYYY-MM-DDTHH:MM:SS.SSSZ
- YYYY-MM-DDTHH:MM:SS.SSS+HHMM
- YYYY-MM-DDTHH:MM:SS.SSS+HH:MM
Data Returned
As a reminder :
- BOOK means the transaction was booked and affects the closing booked balance (status used by this API)
- PDNG means the transaction is about to be booked and does not affect the closing booked balance (status NOT used by this API)
- OTHR means the transaction is not booked and does not affect the closing booked balance or the instant balance (status used by this API)
In addition to mandatory data returned, the optional STET data “entryReference” has been added for all transactions knowing that it is :
- unique value in differed debit transaction life cycle (*)
- identical value before & after transaction settlement (from status “OTHR” to “BOOK”)
(*) Note 1 : except for all schedules of a standing order (considered as one transaction overall)
Note 2 : other types of operations (e. g. Paylib) have this data only for “BOOK” status., except for those rejected
The “entryReference” format is different depending on the type of operations :
| type | length | example |
|---|---|---|
| differed fund transfer | 25 char | 1310400000123480007081059 |
| direct debit | 30 char | 131040000012342014185G10004997 |
| differed debit card | 40 char | 1310400000123420140720170000234978987654 |
| other operations | 40 char | 131040000012342021-02-08-09.33.46.621234 |
The optional STET data “Bank Transaction Code ” (BTC) has been added ONLY for professional & corporate segement clients (CE Net subscribers or equivalent), e.g. for a SEPA SCT Core :
“bankTransactionCode”: {
“domain”: “PMNT”,
“family”: “RCDT”,
“subFamily”: “ESCT”,
“code”: “05”,
“issuer”: “SI MYSYS – Caisse d’Epargne”
}
Example
You can find an example of this request in section “Test our API” and then “Use our sandbox“.
See also STET specifications
Acceptance tests
The purpose of these tests is to ensure that the API complies with the STET standard. They should be validated before any application deployment.
Expected Scope = aisp otherwise specified.
| Test description | Nature of the test | Data set and Expected Result |
|---|---|---|
Retrieve all the transactions linked to a PSU’s account => Check the presence of transactions
| Mandatory | Persona : GEORGES Result : return of the current account transaction history |
Retrieve transactions linked to an unknown account =>HTTP code 404 is returned : {accountId} is invalid | Mandatory | Persona : LEA Result : HTTP code 404 is returned |
HTTP request with an access token which is not authorized to access to this resource (incorrect scope = pisp) => Check that HTTP code 403 is returned – access to resource not allowed | Mandatory | Persona : LEA Result : HTTP code 403 is returned |
HTTP request using POST method => Check that HTTP code 405 is returned | Mandatory | Persona : LEA Result :HTTP code 405 is returned |
Get transactions list with “dateFrom” parameter => Check that the filter is well applied | Mandatory | Persona : GEORGES Result : return of a list of transactions after the date given as input parameter |
Get transactions list with “dateTo” parameter => Check that the filter is well applied | Mandatory | Persona : GEORGES Result :return of a list of transactions before the date given as input parameter, up to the limit of 62 days |
Get transactions list with optional field “entryReference” empty => Check that response field “entryReference” is empty | Mandatory | Persona : GEORGES Result : return a list of transactions with field “entryReference” empty |
Get transactions list with “dateFrom” and “dateTo” parameters => Check that the filter is well applied | Mandatory | Persona : GEORGES Result : return of a list of transactions within the dateFrom and dateTo given as input parameters |
Request with “dateFrom” parameter older than 62 days => Check that HTTP code 400 is returned – Period out of bound expected | Mandatory | Persona : LEA Result : HTTP code 400 is returned |
Request with an invalid “dateFrom” or “dateTo” parameter => Check that HTTP code 400 is returned | Mandatory | Persona : GEORGES Result : HTTP code 400 is returned |
Get no transactions present in the list => Check that HTTP code 204 is returned | Mandatory | Persona : CLAIRE / account FR7617515900000400358074026 Result : HTTP code 204 is returned |
Get PSU's identity
Introduction
This service allows you to retrieve the connected PSU’s identity who has given you their consent to do so (who is not necessarely the customer having the account).
Prerequisites
To proceed with this request, it is necessary to fulfill the eligibility prerequisites and to have retrieved the OAuth2 access token (see in the section “Overview” > “Get your access token“).
To get the PSU’s identity, you need :
- The authorization to transmit this identity information to the TPP must have been transmitted to us via the setting to true of the “psuIdentity” attribute of the PUT /consents method and must not have since been revoked (i.e. not cancel and replace via PUT /consents with a “psuIdentity” attribute set to false);
- The URI to access this method is given through the “_links“: {“endUserIdentity”: {“href”: …}} item as a result to the GET /accounts request.
Request
Method GET /end-user-identity
See also STET specifications
Mandatory or optional settings of the body required to call this service
Mandatory settings : PSU-IP-ADDRESS => to inform if the PSU is connected.
Returned result
This call allows you to get the identity of the end customer
A self link will also be available to return to the page obtained after execution of the request.
This method is limited to a maximum of 4 batch calls per calendar day per TPP + ASPSP + account + PSU. However, when the customer is connected to TPP app and requests an access to his current accounts, the number of access is not limited.
Example
You can find an example of this request in section “Test our API” and then “Use our sandbox“.
See also STET specifications
Acceptance tests
These test cases are intended to allow you to perform a minimum of tests to get started with this API and access it from your application.
| DESCRIPTION OF THE TEST | DATA |
|---|---|
| User identity recovery | Persona : Marc – D0999990I0 Prerequisites : scope OAuth2 = aisp Results : HTTP answer 200 => OK |
| Recovery of the identity of the user who has not given their consent for this | Persona : Tech’n Co – D0999993I0 Prerequisites : scope OAuth2 = aisp Results : HTTP answer 403 => access to the ressource denied |
Get account overdraft
Introduction
Using this service, you can get the authorized overdraft on a payment account granted by the customer.
The type of account is an elligible PDS2 payment account (either a deposit account for individuals, or a current account for professionals or corporate entities).
Prerequisites
The TPP has previously retrieved the list of available accounts for the PSU :
- Customer’s IBAN should have been forwarded to ASPSP in the “overdrafts” list of the PUT /consents method (see use case “Forward customer’s consent“)
- The “accountResourceId” is sent in the GET /accounts response / field “resourceId” for this IBAN
- URI or accessing this method is given using the field “_links”: {“transactions”: {“href”: …}} as a response of the GET /accounts using above “AccountresourceId”
Request
GET /accounts/{accountResourceId}/overdrafts
See also STET specifications
Mandated parameters
“accountResourceId” : current account for which you want to retrieve transactions history.
This field corresponds to the field “resourceId” obtained in the get/accounts request result page.
This method can be called in batch mode up to 4 times per day (per TPP per ASPSP per IBAN per PSU). If the PSU is connected to the TPP, no limits apply.
Example
You can find an example of this request in section “Test our API” and then “Use our sandbox“.
See also STET specifications
Refresh your token
Principle
The refresh token issued by the bank ASPSP is valid up to 180 days and needs to be renewed before it expires. Please also note that :
- Authorization and refresh tokens can be revoked at any moment ;
- If the Authorization token is revoked, then the refresh one is automatically revoked (and the other way round) ;
- The access token has a shorter life cycle (10 to 15min) on standalone device.
How does it work ?
1. You request for a refresh token using POST /token
2. ASPSP :
- Identifies and authenticates the TPP through the presented eIDAS certificate (QWAC)
- Checks the direct or indirect matching between the Authorization Number within the eIDAS certificate and the [client_id] value.
- Controls last PSU SCA date (< 180 jours).
3. If correct, ASPSP then answers through a HTTP200 (OK) that embeds a new autorization token and refresh token that can replace the previous one. You need to store safely these tokens.
4. ASPSP de facto revokes the previous refresh token :
- After timeout of the by-law specified delay between two SCAs ;
- After timeout of the ASPSP specified delay based on internal rules if any ;
- After reject of a request for insufficient scope in order to allow the AISP to request another token with the desired scope ;
- On request of a PSU wanting to revoke the TPP access on his/her account data.
Please also note that, as a TPP, you are able to ask for the revocation of the refresh token through a POST /revoke request.
Revoke the token
A revoke process of the refresh access token (before its expiration @180 days) is possible, see STET specification V1.4.2 / part 1 “Framework” / paragraph 3.4.2.8 “Refresh token revocation”.
Example
You can find an example of this request in the section”Test our API” and then “Sandbox“.
Sandbox
Introduction
This test environment can be used directly via your app : this mode is described hereafter.
Fictive data are used in this context (see use case “Test with persona“).
Prerequisites
The TPP has to declare its APP using our PSD2 Registration API in order to forwerd us :
- its organisation agreement identifier (OID) as defined by your national competent authority
- the public keys of the test QWAC & QSEALC eiDAS compliant certificates
- the callback uri (redirect_uri)
Reminder : you have to get your “AISP” agrement.
Step-by-step approach
1st step : request the access token
This token is mandatory to consume API resources.This call triggers the PSU redirection towards his ASPSP. See the use case “Get your token“.Note : if the PSU has accounts in different ASPSP, you need one access token per ASPSP, and therefore, this request has to be used for each ASPSP.
Our entry point depends on ASPSP code : www.<cdetab>.sandbox.api.89C3.com , and for this environment, the only Caisse d’Epargne available is CE Ile de France with <codetab> = 17515.
Example :
GET https://www.17515.sandbox.api.89C3.com/stet/psd2/oauth/authorizeHeaders :Content-Type : application/x-www-form-urlencoded; charset=utf-8Params: response_type:code
client_id:PSDFR-ACPR-13807
redirect_uri:https://www.mycallback.com/
scope:aisp
Remark :
client_id : your organisation agreement identifier as defined by your national competent authority (PSDXX-YYYY-ZZZZZ).
redirect_uri : callback URL as declared in your APP AND to be forwarded to ASPSP for each sandbox and Go Live requests
2nd step : redirection to PSU screens
Once the redirection is activated, the ASPSP displays to PSU identification and authentification screens.
The UX is shown below :

1) PSU can enter his online banking ID thru the identification screen displayed by the ASPSP.

Note : if PSU is a professional or a corporate, another screen requesting the usage number can be displayed.
2) PSU needs to enter his SCA credentials in the authentication screen.
Different SCA means can be used by the PSU (SMS OTP – see below-, soft token, etc.) :

or for the sandbox.
In some cases, a notification can be sent to the PSU on his/her mobile phone to activate his PSU means, or to finish this step.

3rd step : get the access token
You can get your access token to be able to consume API resources.
If the PSU has authorized the TPP to access to his payment account (successful SCA), a 1-hour validity unique code will be genereted. It will be used for requesting the access_token useful to consumme API methods (see use case “Get your token“).
Example
POST https://www.17515.sandbox.api.89C3.com/stet/psd2/oauth/token
Header :
Content-Type:application/x-www-form-urlencoded; charset=utf-8
Params :
client_id: PSDFR-ACPR-13807
grant_type: authorization_code
code: NnZx1hqHY2CLkCFjiTwhJeflgFedCBa
redirect_uri:https://www.mycallback.com/
Remarks :
client_id : your agreement number as defined by your national competent authority (PSDXX-YYYY-ZZZZZ).
code : data in callback url
redirect_uri : this data needs to be strictly identical to the “redirect_uri” one used in the GET /authorize request !!!
The QWAC eiDAS certificate has to be sent with this request.
Response :
{
“token_type”: “Bearer”,
“expires_in”: 3600,
“scope”: “aisp”,
“refresh_token”: “KUZyspFBZ1R6NqWQdmsZhfdo1nbjK7MoD0Kr2rSi1mSCFNewRfrsH”
}
4th step : use the API methods
1) Get the list of accounts
Once the acces token is received, this methods allows the TPP to list tha payment accounts during the first call (see use case “Get accounts list“).
The TPP sequence is as follows :
- GET /accounts to list all available accounts (without any links nor balances neither transactions)
- ask PSU which accounts & data he wants to authorize TPP to get access to
- PUT /consents for sending to ASPSP the list of authorize accounts
- GET /accounts to access to authorized data
Example BEFORE the PUT /consents method:
GET https://www.17515.sandbox.api.89C3.com/stet/psd2/v1.4.2/accounts
Header :
Authorization: Bearer KXZyspFBZ1R6NqWQdmsZhfdo1nbjK7MoI0Kr2rSi1mSCFNehAbCdEf
X-Request-ID: id-1234567890111121 1
Signature: keyId=\”https://<www.myUrlPath.to>/myQsealCertificate_<footprint sha256>\“, algorithm=\”rsa-sha256\”, headers=\”(request-target) psu-ip-address psu-ip-port psu-http-method psu-date psu-user-agent psu-referer psu-accept psu-accept-charset psu-accept-encoding psu-accept-language digest\”, signature=\”LbkxgICM48J6KdWNaF9qT7OWEorNlAwWNo6R+KkP7cP4TIGkk8wxcsGQXJ9ZnC+ZiA8mjL5S8WQyL41M7iPt+vJX4xh679gdGwmlKzn7E+ZtZ1I4qalRxcdLp4gBL7fll+C2lVBNJrViMJBezFK7AYVjnSWH7t1QiMViAmthebEst=\”
Psu-IP-Address:192.168.0.1
No body
Remarks :
Psu-Ip-Address => allows to differentiate batch request triggered by the TPP from requests whenever connected PSU to TPP app : so this field has to be filled when the PSU is connected
Response : 200 OK
Headers :
X-Request-ID:id-1234567890111121 1
Body :
{
“_links”: {
“self”: {
“templated”: false,
“href”: “/stet/psd2/v1.4.2/accounts”
}
},
“accounts”: [
{
“cashAccountType”: “CACC”,
“accountId”: {
“iban”: “FR7617515000920400430518020”
},
“usage”: “PRIV”,
“psuStatus”: “Account Holder”,
“name”: “LEA SANDBOXA”,
“currency”: “EUR”
},
{
“cashAccountType”: “CACC”,
“accountId”: {
“iban”: “FR7617515000920400851811524”
},
“usage”: “PRIV”,
“psuStatus”: “Account Holder”,
“name”: “LEA SANDBOXA”,
“currency”: “EUR”
}
]
}
Example AFTER the PUT /consents method:
GET https://www.17515.sandbox.api.89C3.com/stet/psd2/v1.4.2/accounts
Header :
Authorization: Bearer KXZyspFBZ1R6NqWQdmsZhfdo1nbjK7MoI0Kr2rSi1mSCFNehAbCdEf
X-Request-ID: id-1234567890111121 1
Signature: keyId=\”https://<www.myUrlPath.to>/myQsealCertificate_<footprint sha256>\“, algorithm=\”rsa-sha256\”, headers=\”(request-target) psu-ip-address psu-ip-port psu-http-method psu-date psu-user-agent psu-referer psu-accept psu-accept-charset psu-accept-encoding psu-accept-language digest\”, signature=\”LbkxgICM48J6KdWNaF9qT7OWEorNlAwWNo6R+KkP7cP4TIGkk8wxcsGQXJ9ZnC+ZiA8mjL5S8WQyL41M7iPt+vJX4xh679gdGwmlKzn7E+ZtZ1I4qalRxcdLp4gBL7fll+C2lVBNJrViMJBezFK7AYVjnSWH7t1QxinDocH1ne=\”
Psu-IP-Address:192.168.0.1
No body
Remarks :
Psu-Ip-Address => allows to differentiate batch request triggered by the TPP from requests whenever connected PSU to TPP app : so this field has to be filled when the PSU is connected
Response : 200 OK
Headers :
X-Request-ID:id-1234567890111121 2
Body
{
“_links”: {
“self”: {
“templated”: false,
“href”: “/stet/psd2/v1/accounts”
}
},
“accounts”: [
{
“cashAccountType”: “CACC”,
“accountId”: {
“iban”: “FR7617515000920400430518020”
},
“resourceId”: “175150009204004305180”,
“_links”: {
“balances”: {
“templated”: false,
“href”: “/stet/psd2/v1/accounts/175150009204004305180/balances”
},
“transactions”: {
“templated”: true,
“href”: “/stet/psd2/v1/accounts/175150009204004305180/transactions”
}
},
“usage”: “PRIV”,
“psuStatus”: “Account Holder”,
“name”: “LEA SANDBOXA”,
“currency”: “EUR”
},
{
“cashAccountType”: “CACC”,
“accountId”: {
“iban”: “FR7617515000920400851811524”
},
“resourceId”: “175150009204008518115”,
“_links”: {
“balances”: {
“templated”: false,
“href”: “/stet/psd2/v1/accounts/175150009204008518115/balances”
},
“transactions”: {
“templated”: true,
“href”: “/stet/psd2/v1/accounts/175150009204008518115/transactions”
}
},
“usage”: “PRIV”,
“psuStatus”: “Account Holder”,
“name”: “LEA SANDBOXA”,
“currency”: “EUR”
}
]
}
2) Send PSU consent to ASPSP
See use case “Forward PSU consent“.
Example :
PUT https://www.17515.sandbox.api.89C3.com/stet/psd2/v1.4.2/consents
Headers :
Authorization: Bearer KXZyspFBZ1R6NqWQdmsZhfdo1nbjK7MoI0Kr2rSi1mSCFNehAbCdEf
X-Request-ID: id-1234567890111121 2
Signature: keyId=\”https://<www.myUrlPath.to>/myQsealCertificate_<footprint sha256>\“, algorithm=\”rsa-sha256\”, headers=\”(request-target) psu-ip-address psu-ip-port psu-http-method psu-date psu-user-agent psu-referer psu-accept psu-accept-charset psu-accept-encoding psu-accept-language digest\”, signature=\”LbkxgICM48J6KdWNaF9qT7OWEorNlAwWNo6R+KkP7cP4TIGkk8wxcsGQXJ9ZnC+ZiA8mjL5S8WQyL41M7iPt+vJX4xh679gdGwmlKzn7E+ZtZ1I4qalRxcdLp4gBL7fll+C2lVBNJrViMJBezFK7AYVjnSWH7t1QinCept10n=\”
Psu-IP-Address:192.168.0.1
Body
{
“balances”: [
{
“iban”: “FR7617515000920400430518020”
},
{
“iban”: “FR7617515000920400851811524”
}
],
“transactions”: [
{
“iban”: “FR7617515000920400430518020”
},
{
“iban”: “FR7617515000920400851811524”
}
],
“trustedBeneficiaries”: false,
“psuIdentity”: false
}
Response :
201 « Created »
Headers :
X-Request-ID:id-1234567890111121 2
No body
3) Get the balances
See use case “Accounting balances“.
Example :
GET https://www.17515.sandbox.api.89C3.com/stet/psd2/v1.4.2/accounts/{accountResourceId}/balances
Headers :
Authorization: Bearer KXZyspFBZ1R6NqWQdmsZhfdo1nbjK7MoI0Kr2rSi1mSCFNehAbCdEf
X-Request-ID: id-1234567890111121 2
Signature: keyId=\”https://<www.myUrlPath.to>/myQsealCertificate_<footprint sha256>\“, algorithm=\”rsa-sha256\”, headers=\”(request-target) psu-ip-address psu-ip-port psu-http-method psu-date psu-user-agent psu-referer psu-accept psu-accept-charset psu-accept-encoding psu-accept-language digest\”, signature=\”LbkxgICM48J6KdWNaF9qT7OWEorNlAwWNo6R+KkP7cP4TIGkk8wxcsGQXJ9ZnC+ZiA8mjL5S8WQyL41M7iPt+vJX4xh679gdGwmlKzn7E+ZtZ1I4qalRxcdLp4gBL7fll+C2lVBNJrViMJBezFK7AYVjnSWH7t1Qincept10n=\”
Response :
200 OK
Headers :
X-Request-ID:id-1234567890111121 2
Body :
{
“balances”: [
{
“balanceType”: “CLBD”,
“name”: “Solde comptable au 28/09/2018”,
“balanceAmount”: {
“amount”: “-150.00”,
“currency”: “EUR”
}
}
],
“_links”: {
“self”: {
“templated”: false,
“href”: “/stet/psd2/v1/accounts/175150009204004305180/balances”
},
“transactions”: {
“templated”: true,
“href”: “/stet/psd2/v1/accounts/175150009204004305180/transactions”
},
“parent-list”: {
“templated”: false,
“href”: “/stet/psd2/v1/accounts”
}
}
}
4) Get transactions history
See use case “Get transactions history“.
Example :
GET https://www.17515.sandbox.api.89C3.com/stet/psd2/v1.4.2/accounts/{accountResourceId}/transactions
Headers :
Authorization: Bearer KXZyspFBZ1R6NqWQdmsZhfdo1nbjK7MoI0Kr2rSi1mSCFNehAbCdEf
X-Request-ID: id-1234567890111121 1
Signature: keyId=\”https://<www.myUrlPath.to>/myQsealCertificate_<footprint sha256>\“,algorithm=\”rsa-sha256\”,headers=\”(request-target) psu-ip-address psu-ip-port psu-http-method psu-date psu-user-agent psu-referer psu-accept psu-accept-charset psu-accept-encoding psu-accept-language digest\”,signature=\”LbkxgICM48J6KdWNaF9qT7OWEorNlAwWNo6R+KkP7cP4TIGkk8wxcsGQXJ9ZnC+ZiA8mjL5S8WQyL41M7iPt+vJX4xh679gdGwmlKzn7E+ZtZ1I4qalRxcdLp4gBL7fll+C2lVBNJrViMJBezFK7AYVjnSWH7t1T0tOtuTuT1ti=\”
Psu-IP-Address:192.168.0.1
No body
Response :
200 OK
Headers :
X-Request-ID:id-1234567890111121 1
Body
{
“_links”: {
“balances”: {
“templated”: false,
“href”: “/stet/psd2/v1/accounts/175150009204004305180/balances”
},
“self”: {
“templated”: true,
“href”: “/stet/psd2/v1/accounts/175150009204004305180/transactions”
},
“parent-list”: {
“templated”: false,
“href”: “/stet/psd2/v1/accounts”
}
},
“transactions”: [
{
“resourceId”: null,
“remittanceInformation”: [
“Retrait Carte”
],
“entryReference”:”751040043051802019-09-08-05.33.46.621234″,
“transactionAmount”: {
“amount”: “13.00”,
“currency”: “EUR”
},
“bookingDate”: “2019-09-05”,
“creditDebitIndicator”: “DBIT”,
“status”: “BOOK”
}
]
}
5) Get PSU Identity
See use case “Get PSU identity“.
Example :
GET https://www.12579.sandbox.api.89C3.com/stet/psd2/v1.4.2/end-user-identity
6) Get the overdraft
See use case “Get account overdraft“.
Example :
GET https://www.17515.sandbox.api.89C3.com/stet/psd2/v1.6.2/accounts/175159000004003580740/overdrafts
Headers :
Authorization: Bearer KXZyspFBZ1R6NqWQdmsZhfdo1nbjK7MoI0Kr2rSi1mSCFNehAbCdEf
X-request-id: id-1234567890111121 7
Signature: keyId=\”https://<www.myUrlPath.to>/myQsealCertificate_<empreinte sha256>\“,algorithm=\”rsa-sha256\”,headers=\”(request-target) psu-ip-address psu-ip-port psu-http-method psu-date psu-user-agent psu-referer psu-accept psu-accept-charset psu-accept-encoding psu-accept-language digest\”,signature=\”LbkxgICM48J6KdWNaF9qT7OWEorNlAwWNo6R+KkP7cP4TIGkk8wxcsGQXJ9ZnC+ZiA8mjL5S8WQyL41M7iPt+vJX4xh679gdGwmlKzn7E+ZtZ1I4qalRxcdLp4gBL7fll+C2lVBNJrViMJBezFK7AYVjnSWH7t1T0tOtuTuT1ti=\”
Psu-IP-Address: 192.168.0.1
Pas de body
Réponse : 200 (=> OK)
Headers :
X-request-id: id-1234567890111121 7
Content-Type: application/hal+json;charset=UTF-8
Body :
{
“overdrafts”: {
“allowedAmount”: {
“amount”: 0,
“currency”: “EUR”
}
},
“_links”: {
“self”: {
“href”: “/stet/psd2/v1.6.2/accounts/175159000004003580740/overdrafts”,
“templated”: false
},
“balances”: {
“href”: “/stet/psd2/v1.6.2/accounts/175159000004003580740/balances”,
“templated”: false
},
“transactions”: {
“href”: “/stet/psd2/v1.6.2/accounts/175159000004003580740/transactions”,
“templated”: true
},
“parent-list”: {
“href”: “/stet/psd2/v1.6.2/accounts”,
“templated”: false
}
}
}
7) Refresh your access token
See use case “Refresh your token“.
Example :
POST https://www.12579.sandbox.api.89C3.com/stet/psd2/oauth/token
Header :
Content-Type : application/x-www-form-urlencoded; charset=utf-8
Params:
client_id: PSDFR-ACPR-13807
grant_type: refresh_token
refresh_token: KUZyspFBZ1R6NqWQdmsZhfdo1nbjK7MoD0Kr2rSi1mSCFNehAbCdEf
Response :
{
“token_type”: “Bearer”,
“expires_in”: 3600,
“scope”: “aisp offline_access”,
“refresh_token”: “KUZyspFBZ1R6NqWQdmsZhfdo1nbjK7MoD0Kr2rSi1mSCFNehAbCdEf”
}
Test with persona
Introduction
As required by PSD2 regulation (see RTS Art. -30 (5)), we deliver a testing facility, including support, for connection and functional testing using non-real test data. These persona are gathered using banking segments (retail, corporate) and customer segmentation (student, young active, professionnal, retired, etc…).
Expected API input data are listed (PSU id, IBAN). PSU consent has already been recorded. These data included the accounting balance are static (no changes).
Please note that this test dataset will evolve overtime with additional profiles and data history (volume, depth). So stay informed and visit this dev portal regularly!
PSU ID & TEST DATA AS DESCRIBED BELOW CANNOT BE USED IN PRODUCTION LIVE ENVIRONMENT.
Persona
Image

| Image

|
LEA SANDBOXA
| CLAIRE RECETTEB
|
Image

| Image

|
GEORGES PERSONAC
| GILLES TESTUNID
|
Please note that in the assembly mode, you’ll have to enter OTP SMS = « 12345678 » for all persona whenever the authentication screen is proposed.
WARNING : NEW ID NUMBER
| Persona | Segment | New Id | Bank code | IBAN | Payment account holder | PSU consent : balance/ Transactions / Identity | Balance | Currency |
|---|---|---|---|---|---|---|---|---|
| LEA SANDBOXA | Particulier | 9999999901 | 17515 | FR7617515000920400430518020 | LEA SANDBOXA | TRUE TRUE FALSE | -150.00 | EUR |
| CLAIRE RECETTEB | Particulier | 9999999902 | 17515 | FR7617515900000400358074026 | CLAIRE RECETTEB | TRUE TRUE FALSE | 0.00 | EUR |
| CLAIRE RECETTEB | Entrepreneur individuel | 9999999902 | 17515 | FR7617515900000800358074006 | CLAIRE RECETTEB | TRUE TRUE FALSE | +23766.98 | EUR |
| GEORGES PERSONAC | Particulier | 9999999903 | 17515 | FR7617515000920400085945890 | Mr et Mme GEORGES PERSONAC | TRUE TRUE FALSE | +10.00 | EUR |
| GILLES TESTUNID | Particulier | 9999999904 | 17515 | FR7617515000920440878790811 | Mr GILLES TESTUNID | TRUE TRUE FALSE | +11880.30 | EUR |
| GILLES TESTUNID | Particulier | 9999999904 | 17515 | FR7617515000920402428687756 | Mr OU Mme GILLES TESTUNID | TRUE TRUE FALSE | 0.00 | EUR |
| GILLES TESTUNID | Particulier | 9999999905 | 17515 | FR7617515000920402428748381 | Mr ET Mme GILLES TESTUNID | TRUE TRUE FALSE | +5879.22 | EUR |
API version decommissioning policy
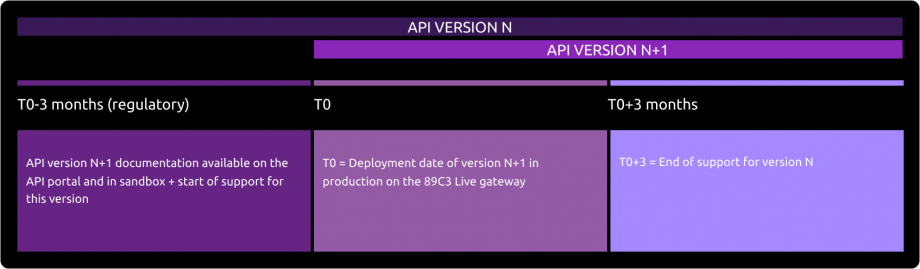
According to API product life cycle, an API version can be deprecated (meaning this API is not any more accessible on gateways and sandbox).
An overlap period between two major API releases is provided as described below :
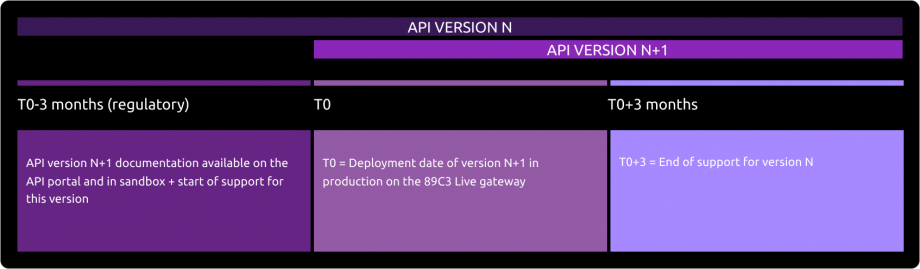
The communication around the decommissioning process of a version N will be done at the release date of version N+1 through this portal / “roadmap” section.
Roadmap
This API can evolve. Please note that API modifications can occur out of the three-month regulatory notice period (art. 30 des RTS / paragraphe 4). We apply this in case of :
- urgent functional issue to solve impacting all PSU of at least one major customers segment
- security issue
- evolutions requested by the national competent authority
Please do find below our forecast roadmap :
| Our API version | Features | Deployment date Dev Portal & Sandbox | Deployment date BPCE Live API Gateway | Deprecation date BPCE Live API Gateway |
|---|---|---|---|---|
| v1.6.2 | API Version v1 :
API version v1.4.2 = API version v1 +
API version v1.6.2 = API version v1.4.2 +
| October 20, 2022 | Februray 08, 2023 | To be announced |
Functional limits
Limits of this API version
- Apply only to active and eligible online accessible payment accounts in euro currrency (the determining criterion for the purposes of that categorisation lies in the ability to perform daily payment transactions from such an account managed by the central backend IT system, source of data sent back thru APIs)
- Use AISP-mix model (PUT /consents method is mandatory for sending customer consent to ASPSP)
- Use only authentication with redirect mode (Strong Customer Authentication required and handled by the bank which IS NOT an obstacle according to French national competent authority
Note : TPP are not allowed to send to ASPSP the PSU credentials, and only ASPSP SCA redirect screens can be used (no embeding process as clarified by European Banking Authority based on articles PSD2 #95.5 & RTS #31)
- Access to the list of trusted beneficiaries using GET /trustedBeneficiaries is NOT available (feature not implemented in Caisse d’Epargne online banking service interfaces)
- Access to customer account holder identity (first name and last name) is NOT available
- Transaction history data depth is aligned on online banking services (62-day period max for retail cutomers & small professionals/entrepreneurs segments, 90-day period max for large professionals & corporates, limited to 500 operations, no paginations managed by the API in both cases)
- “aisp extended_transaction_history” mode is NOT supported
- Access to payment account is done only using IBAN as main parameter
- There are no rate limits if the PSU-IP-ADDRESS is supplied, otherwise limited to 4 calls (see PSD2 regulations) :
- per calendar day (00h00 – 23h59:59:999)
- per TPP OID
- per ASPSP end point
- per PSU ID
- per IBAN
- per API AIS method (/!\ /transactions method with or without dateFrom / dateTo parameters is considered as one method)
- The optional STET data “entryReference” applies only to PART & PRO/EI customer segments (see the functional perimeter in use case “Get transactions history”)
- The optional STET data “dateType” is not supported
Note : as this data is issued on the spot via API, the search using “entryReferenceFrom” and/or “entryReferenceto” parameters is NOT supported
Limits related to eligible payment accounts
Apply to the following customer segments :
- Retail customer who subscrided direct access “DEI PART” online banking. In this case, the payment account starting with 04 is called a “deposit account”, and includes joint account, as well as attached minor to the account family.
Note 1 : the legal guardian or representative using Web Protexion solution (for managing persons under tutorship / curatorship) is not supported
Note 2 : a retail customer is a “physical individual” having the legal status of “capable adult”. He/she may have small professionals activities using the legal status “individual entrepreneur”, and is considered as a retail customer
- Large professional & corporate using direct access “CE Net” online banking (having a subcription “CE Net Compte” and an account starting with 08 with electronic funds tranfers and electronic debits activated) have the status of “legal entity” (in this case, the payment account is called “current account”)
Limits related to SCA means compliant with this API
- Retail PSU equiped with (password + SMS OTP) and/or (CAP reader) and/or (Sécur’Pass on smartphone)
- Professional PSU equiped with (password + SMS OTP) and/or (CAP reader) and/or (Sécur’Pass on smartphone)
- Corporate & association PSU equiped with (password + SMS OTP) and/or (CAP reader) and/or (physical token TurboSign) and/or (Sécur’Pass on smartphone)
Note : if the PSU is only equiped with a physical token, this SCA mean can’t be used on his/her mobile/smartphone
From test to live data
According to PDS2 regulation, the data set available thru this dev portal, Try-it mode and sandbox are based on fictive data (or non-real ones).These data are described in the use case “Test our API“.
In order to access to live data, please use first our PSD2 Registration API.
IMPORTANT NOTE : a weekly slot is reserved for a programmed maintenance (all IT infrastructure incl’d backends and API gateways) Monday morning from midnight to 06:00 am CET, and could generate some perturbations during this period (same for some banking batch processes initiated at the beginning or at the end of the day/month/quarter/year).
For live operations, the parameter “bank code” allows to send API requests to the right ASPSP backend thru a dedicated « endpoint » www.<bank code>.oba-bad-me-live.api.89c3.com(or www.<bank code>.oba-bad-me-live.api.caisse-epargne.fr aligned on direct access domain name www.caisse-epargne.fr).
(new URL to be taken into account from now on)
(As a reminder, the existing URL www.<codetab>.live.api.89C3.com will no longer be available as of 28/09/2025)
Once chosen, this entry point shall also be used for all subsequent requests :
| Bank code | Bank name | Bank short name | Available in Try-it and Sandbox | Available in production |
|---|---|---|---|---|
| 11315 | Caisse d’Epargne Provence Alpes Corse | CEPAC | – | Yes |
| 11425 | Caisse d’Epargne Normandie | CEN | – | Yes |
| 12135 | Caisse d’Epargne Bourgogne Franche-Comté | CEBFC | – | Yes |
| 14445 | Caisse d’Epargne Bretagne-Pays de Loire | CEBPL | – | Yes |
| 13135 | Caisse d’Epargne Midi-Pyrénées | CEMP | – | Yes |
| 13335 | Caisse d’Epargne Aquitaine Poitou-Charentes | CEAPC | – | Yes |
| 13485 | Caisse d’Epargne Languedoc-Roussillon | CELR | – | Yes |
| 13825 | Caisse d’Epargne Rhône Alpes | CERA | – | Yes |
| 14265 | Caisse d’Epargne Loire Drôme Ardèche | CELDA | – | Yes |
| 14505 | Caisse d’Epargne Loire-Centre | CELC | – | Yes |
| 17515 | Caisse d’Epargne Ile De France | CEIDF | Yes | Yes |
| 18315 | Caisse d’Epargne Côte d’Azur | CECAZ | – | Yes |
| 18715 | Caisse d’Epargne Auvergne et Limousin | CEPAL | – | Yes |
| 15135 | Caisse d’Epargne Grand Est Europe | CEGEE | – | Yes |
| 16275 | Caisse d’Epargne Hauts de France | CEHDF | – | Yes |
| 12579 | Banque BCP | BBCP | – | Yes |
| 30258 | BTP Banque | BTPB | – | Yes |
| 42559 | Crédit Coopératif | CCO | – | Yes |
Eligibility
The API resources can only be used by Payment Service Providers (PSP) having a Account Information Service Providers (AISP) role.
In order to provide a service to users of account informations services under PSD2 directive, you must be a licenced PSP such as credit institution, electronic money institution, and payment institution. This status is delivered by the financial authorities of the country where the request is made ; in France it is the “Autorité de Contrôle Prudentiel et de Résolution (ACPR), under the supervision of the Banque de France regulatory body :
Obtaining and maintaining such agreement requires rigorous procedures in order to give strong guarantees to the account informations services users. The forms are provided on the ACPR website : https://acpr.banque-france.fr/en/authorisation/banking-industry-procedures/all-forms
Once the agrement is granted, the Organisation Identifier (OID) given by the national authority has the following format (UPPER case):
PSDXX-YYYYYYYY-ZZZZZZZZ
“PSD” as 3 character legal person identity type reference
2 character ISO 3166 country code representing the NCA country
hyphen-minus “-” (0x2D (ASCII), U+002D (UTF-8)); and
2-8 character NCA identifier (A-Z uppercase only, no separator)
hyphen-minus “-” (0x2D (ASCII), U+002D (UTF-8)); andPSP identifier (authorization number as specified by NCA)
This OID is very important to identify yourself as a TPP :
- using STET API requests as OID is included in the parameter “client_ID”
- using mutual authentication (TLS) as OID is included in eIDAS certificates to be delivered to the bank (see below)
Please note that if you are using our “PSD2 Registration” API, an internal OID will be generated & shall be used for subsequent API requests.
You also need eIDAS (electronic IDentification And trust Services) compliant certificates delivered by a Qualified Certification Service Provider (QTSP, see list available on https://webgate.ec.europa.eu/tl-browser/#/).
In order to be able to consume PSD2 API published on our BPCE Portal, the TPP has to enroll its app and to use live certificates signed by a QTSP while sending PSD2 Registration API requests :
- a set of QWAC (for securing the TLS) and QSEALC (to be stored in our gateway) certificates for the sandbox
- another set of (for securing the TLS) and QSEALC (to be stored in our gateway) certificates for the live environment
Note : in case of certificate renewal, and if the QTSP is different (or the same but using different root key elements), the TPP must advise our API support at least 2 months prior the change in order to be able to double check if the new certification authority is loaded on our infrastructure.
A keyID shall also be provided with a correct STET format integrating the SHA256 certificate fingerprint after “_” char, see example STET / Documentation Part 3: Interaction Examples / section 6. AISP Use cases / Signature : keyId=https://path.to/myQsealCertificate_612b4c7d103074b29e4c1ece1ef40bc575c0a87e.
Please embed only public keys. Controls on other data will be based on European Banking Association TPP register (https://euclid.eba.europa.eu/register/pir/disclaimer).
You can also refer to the FAQ section.
History
STET Compliance
This REST API complies with the French interbank specification STET (https://www.stet.eu/en/psd2/), version v.1.6.2.0, in order to meet the regulatory requirements of PSD2. It takes into account the functional limitations specific to this retail bank described in the “Limitations” section.
As a reminder:
- the texts of Payment Directive number 2 (PSD2, EU reference 2015/2366 of 25/11/2015) came into force on 13 January 2018: http://eur-lex.europa.eu/legal-content/FR/TXT/?uri=CELEX:32015L2366
- They have been supplemented by regulatory technical standards (RTS, EU Delegated Regulation 2018/389) relating to strong customer authentication and common secure open communication standards, which will come into force on 14 September 2019. These standards are the RTS (Rules Technical Standards): https://eur-lex.europa.eu/legal-content/FR/TXT/?toc=OJ%3AL%3A2018%3A069%3ATOC&uri=uriserv%3AOJ.L_.2018.069.01.0023.01.FRA
In France, Order 2017-1252 of 9 August 2017 transposes the PSD2 Directive into the legislative part of the Monetary and Financial Code. The Order is supplemented at regulatory level by Decrees 2017-1313 and 2017-1314 of 31 August 2017 and the five Orders of 31 August 2017.
| Our API version | STET standard version |
|---|---|
| v1.6.2 | v1.6.2.0 |
You can refer to the STET documentation.
Description of TPP support
According to Article 30 (5) of the RTS, a support for third-party providers is available. This support can be joined via the form on this Groupe BPCE API Store. Responses are sent during office opening hours (09:00 – 18:00 Central European local Time) even so a 24h/7d monitoring process of our IT systems exists.
Its general principle is shown below, taking into account delays of Article 30 (4) of the RTS :
Release notes
Important changes made since the first release of this documentation was published :
| MÉTHODE(S) | DATE | DESCRIPTION DE L’ÉVOLUTION |
|---|---|---|
| All | October 20, 2022 | Alignment on PSD2 API STET v1.6.2.0 |










